BY: ADAM BAER, DIRECTOR OF IT SERVICES
As an IT director, I am occasionally asked questions like “What do you think is the biggest threat in cybersecurity today?”
I believe when people ask me this question, they expect to hear about some new form of ransomware that will soon be terrorizing networks. Or, perhaps they’re looking for a more abstract answer about how the sophistication of cybercriminals means there’s always a new “biggest threat” and the real challenge is staying on top of it.
There’s a bit of substance in those ideas, but the real truth any IT professional will tell you (if they’re feeling candid enough) is that any business’s single greatest cybersecurity risk is its own employees.
For many, the word “cybersecurity” still conjures up memories of the antivirus software that comes natively installed on some personal computers, or maybe ideas about “hacking” that came from a scene on CSI or Law & Order. As an IT professional, one of my objectives is to make them think instead about the cybersecurity habits they don’t even realize they’re engaging in.
And if that fails, my job is to help them have solutions in place that protect their business from itself.
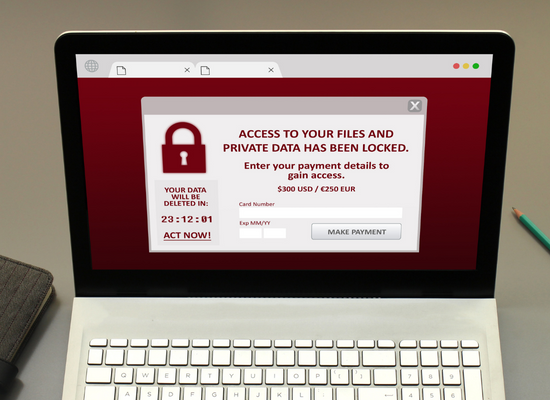
DANGER FROM WITHIN
Is this framing a little bit overly dramatic? Maybe, but let’s take a look at the facts. According to a 2022 Data Breach Investigations report produced by Verizon, 85% of all data breaches involve some form of human interaction.
Whether it’s email phishing, domain spoofing/fake websites, scareware (which misleads users into believing their computer is infected and downloading malicious code to “fix” it), or any of several other choice methods, most cybersecurity threats have a common theme. That theme is social engineering – the use of psychological manipulation to trick people into making cybersecurity mistakes or giving away sensitive/confidential information.
The reason is simple: most of the time it is easier to deceive an unsuspecting human being than it is to crack an otherwise secure piece of software. Most people have heard of ransomware and know well enough to be afraid of it. Fewer people realize that ransomware is usually allowed onto a network by somebody clicking a risky link or downloading a file without thinking twice about it.
And beyond social engineering, many users practice poor cyber hygiene. Whether it’s weak passwords that rely on memorization, failing to utilize tools like VPNs or multi-factor authentication, or connecting to the company network with unsecured personal devices, all of these habits can put your network at risk.
Disturbingly, fewer than half of Americans (45%) say they would change their password after a data breach. Think for a moment about how many high-profile data breaches you’ve heard about in recent years. Have you ever known somebody who uses something like “Password” or “(Spouse name)1!” for every login credential, even at work? Imagine if that password could be used to access every important asset on your network, and wound up being compromised in a third-party data breach. It’s enough to set my mind spinning.
So what can be done about it?
SECURING YOUR NETWORK, ONE LAYER AT A TIME
One concept I often find myself repeating is that network security is like any type of security: there is no “silver bullet” solution. Many businesses have a VPN and a firewall, and many assume that alone is enough. This is a dangerous assumption. If you think of your network as a physical building, your firewall is roughly equivalent to closing and locking the front door. It’s very important, but it’s just one layer of security.
Tech’s physical security experts would tell you that a locked door ought to be supplemented by access control, video surveillance, intrusion detection, and more. Each of those solutions adds a layer of security that reinforces the others. Likewise, it’s important to add layers to your network.
A password manager application can help protect your business from compromised login credentials. Multi-factor authentication can provide another barrier to entry, even if those passwords are somehow obtained by bad actors. A Backup and Recovery plan can help make your business resilient against a potential ransomware attack. An Endpoint Detection and Response (EDR) solution provides proactive monitoring, threat identification and containment, and real-time analysis tools.
Guided training can help your employees identify phishing and other types of social engineering attacks, and reinforce the importance of maintaining strong cyber hygiene both in and out of the workplace. And if that training fails to take hold and produce better habits, a Zero Trust Architecture can provide the ultimate level of enforced network security.
I appreciate that it can be intimidating to approach the challenge of going from minimal network security to a fully reinforced system. Many businesses lack the resources and bandwidth to undergo these changes alone. However, with the help of a capable IT partner, I believe any business is capable of identifying and shoring up its risk factors, and greatly improving its cybersecurity profile. Doing so takes time and effort, but it’s worth it, for the peace of mind of knowing the network your business relies on is safe from its biggest threats, both internal and external.



